
High-performance computer networks, some belonging to the world’s most prominent organizations, are under attack by a newly discovered backdoor that gives hackers the ability to remotely execute commands of their choice, researchers said on Tuesday.
Kobalos, as researchers from security firm Eset have named the malware, is a backdoor that runs on Linux, FreeBSD, and Solaris, and code artifacts suggest it may have once run on AIX and the ancient Windows 3.11 and Windows 95 platforms. The backdoor was released into the wild no later than 2019, and the group behind it was active throughout last year.
Multistriped backdoor
While the Kobalos design is complex, its functionalities are limited and almost entirely related to covert backdoor access. Once fully deployed, the malware gives access to the file system of the compromised system and enables access to a remote terminal that gives the attackers the ability to run arbitrary commands.
In one mode, the malware acts as a passive implant that opens a TCP port on an infected machine and waits for an incoming connection from an attacker. A separate mode allows the malware to convert servers into command-and-control servers that other Kobalos-infected devices connect to.
Infected machines can also be used as proxies that connect to other servers compromised with Kobalos. These proxies can be chained so that the operators can use multiple Kobalos-compromised machines to reach their final targets.
The figure below shows an overview of the Kobalos features:
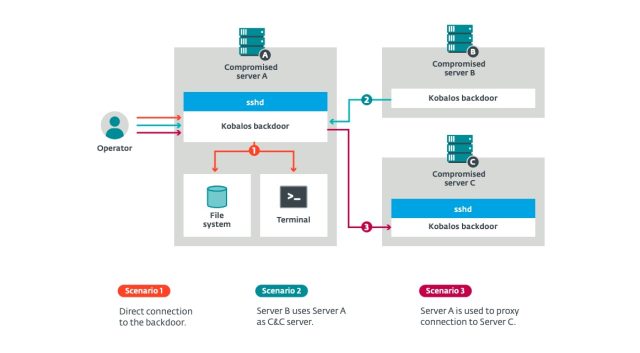
To maintain stealth, Kobalos encrypts communications with infected machines using two 16-byte keys that are generated and then encrypted with a password-protected RSA-512 private key. All inbound and outbound traffic from then on is RC4-encrypted using the two keys. The malware uses a complex obfuscation mechanism that makes third-party analysis difficult.
Small number of elite targets
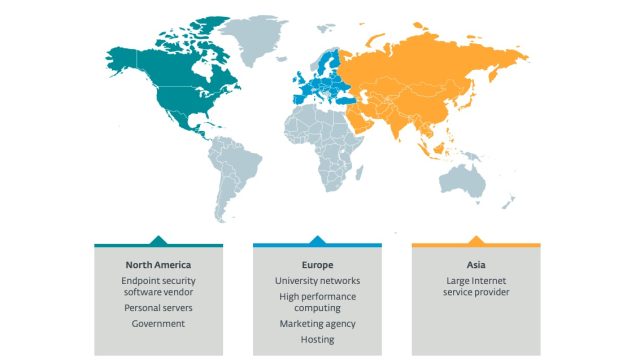
Those infected with the malware include a university, an end-point security company, government agencies, and a large ISP, among others. One high-performance computer compromised had no less than 512 gigabytes of RAM and almost a petabyte of storage.
Eset said the number of victims was measured in the tens. The number comes from an Internet scan that measures behavior that occurs when a connection is established with a compromised host from a specific source port. The image below shows that the victims were located in the United States, Europe, and Asia:
The robustness of the malware, combined with the small number of prominent targets, demonstrates that Kobalos is the work of an advanced team of hackers, particularly in the less-traveled path of non-Windows-based malware.
“The numerous well-implemented features and the network evasion techniques show the attackers behind Kobalos are much more knowledgeable than the typical malware author targeting Linux and other non-Windows systems,” Eset researchers Marc-Etienne M.Léveillé and Ignacio Sanmillan wrote in a report. “Their targets, being quite high-profile, also show that the objective of the Kobalos operators isn’t to compromise as many systems as possible. Its small footprint and network evasion techniques may explain why it went undetected until we approached victims with the results of our Internet-wide scan.”
So far, it’s not clear how Kobalos is getting installed. A component that steals credentials that administrators used to log in to machines using the SSH protocol is one possibility, but it's unlikely it's the sole means of infection. It's also unclear precisely what the Kobalos operators are doing with the malware. There were no signs that compromised systems were used to mine cryptocurrency or carry out other compute-intensive tasks.
“The intent of the authors of this malware is still unknown,” they wrote. “We have not found any clues to indicate whether they steal confidential information, pursue monetary gain, or are after something else.”
reader comments
45